Throttling and Blocking Bad Requests in Phoenix Web Applications with PlugAttack
https://www.paraxial.io/blog/throttle-requests
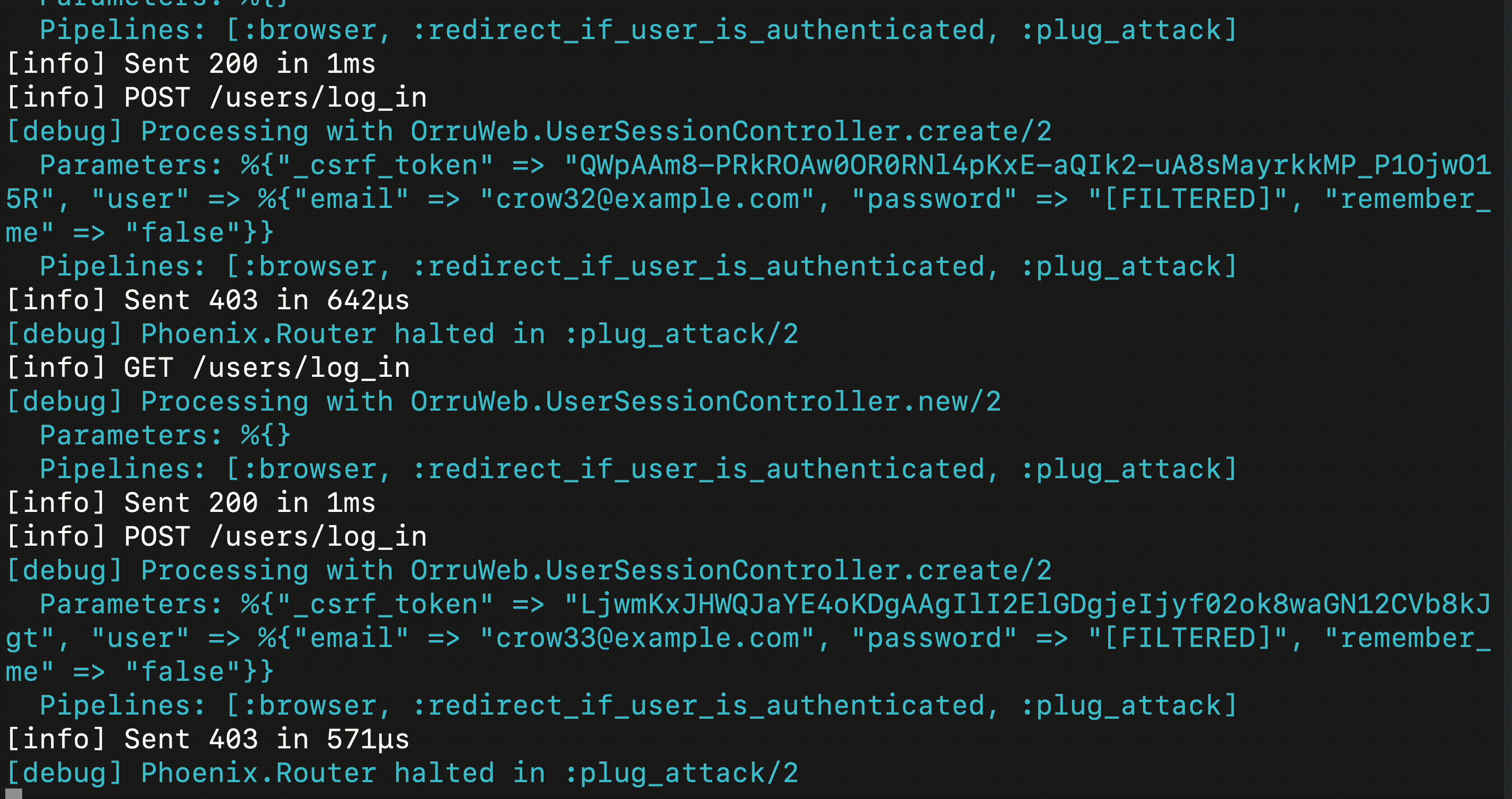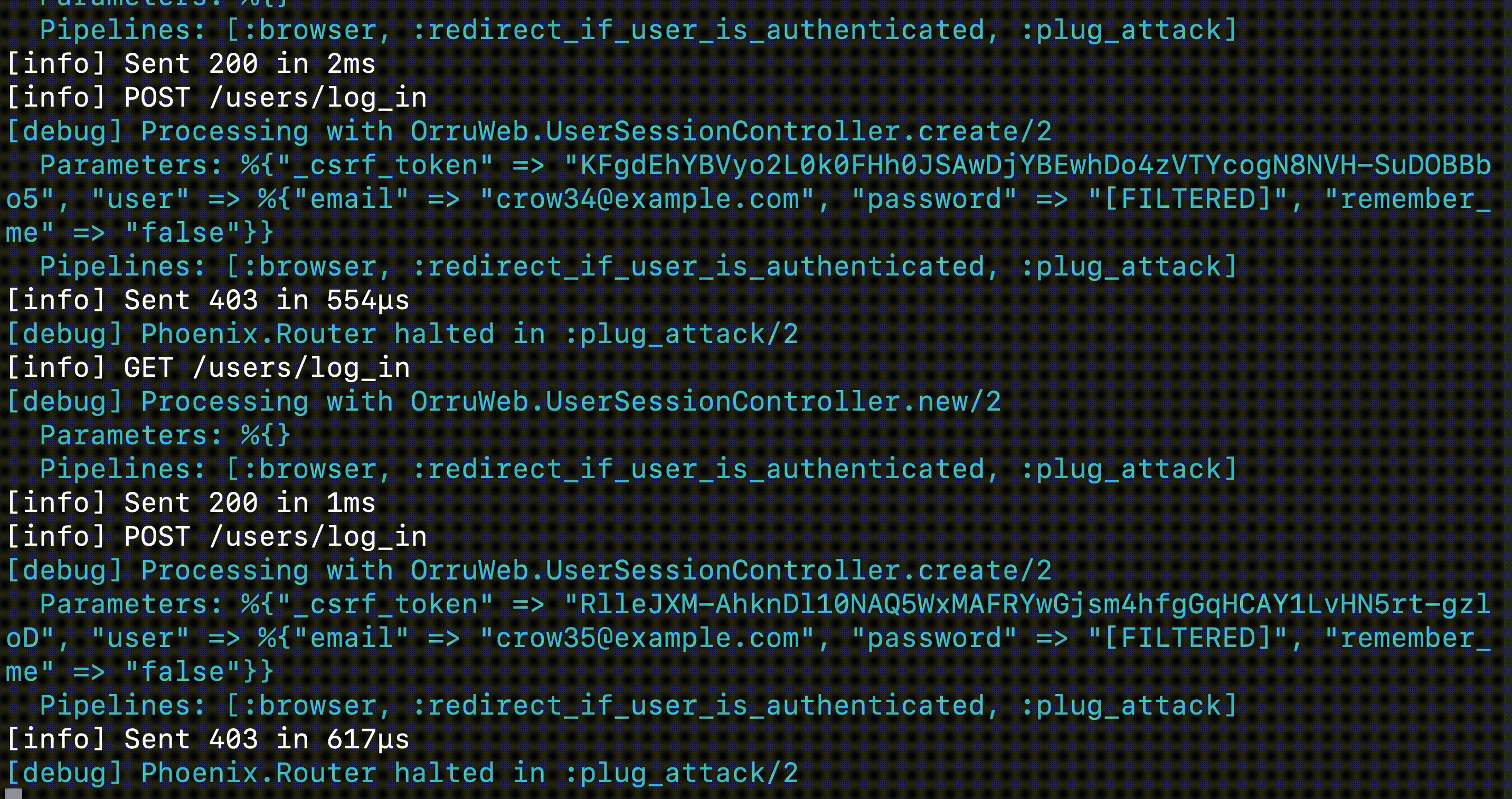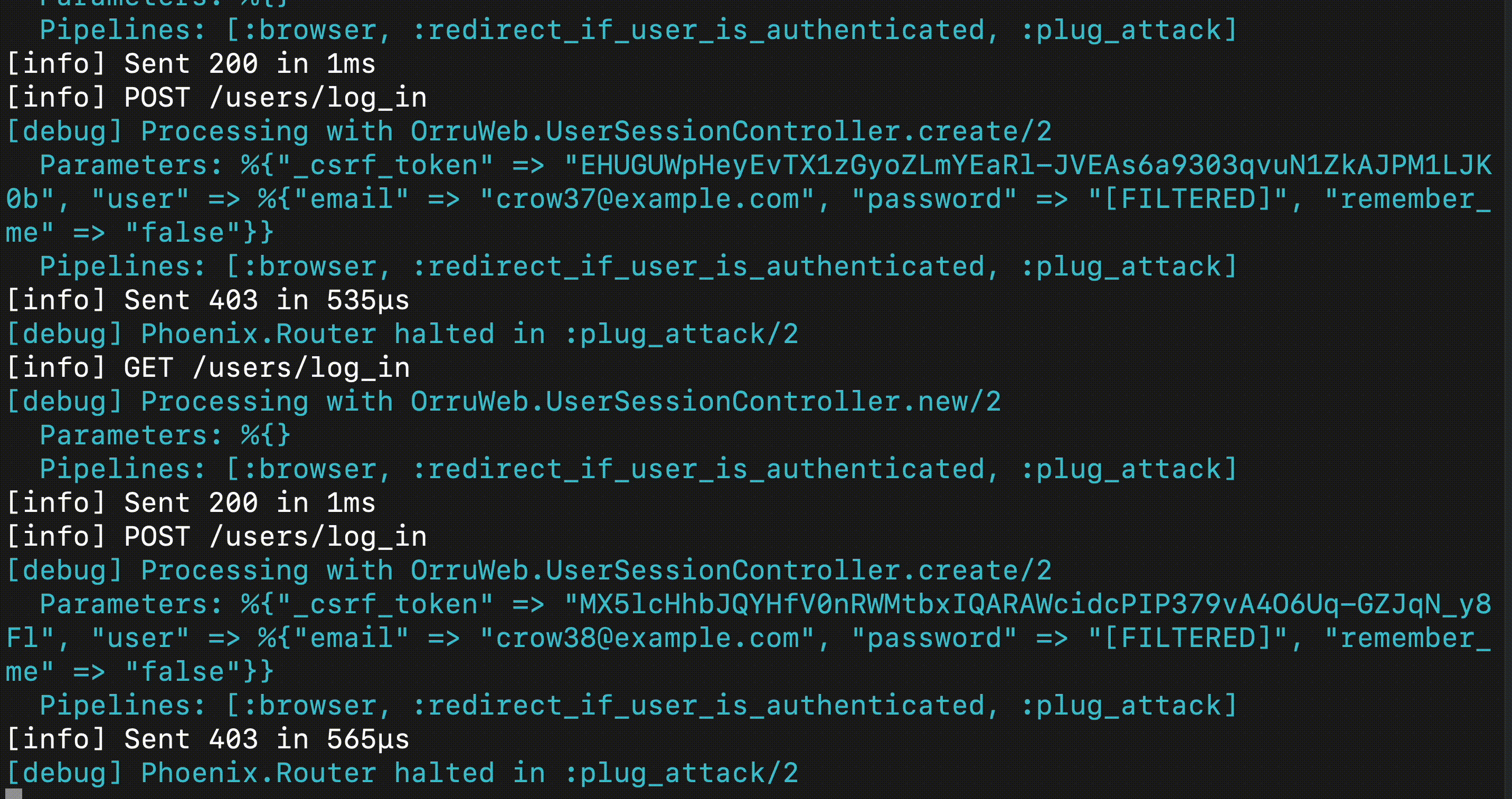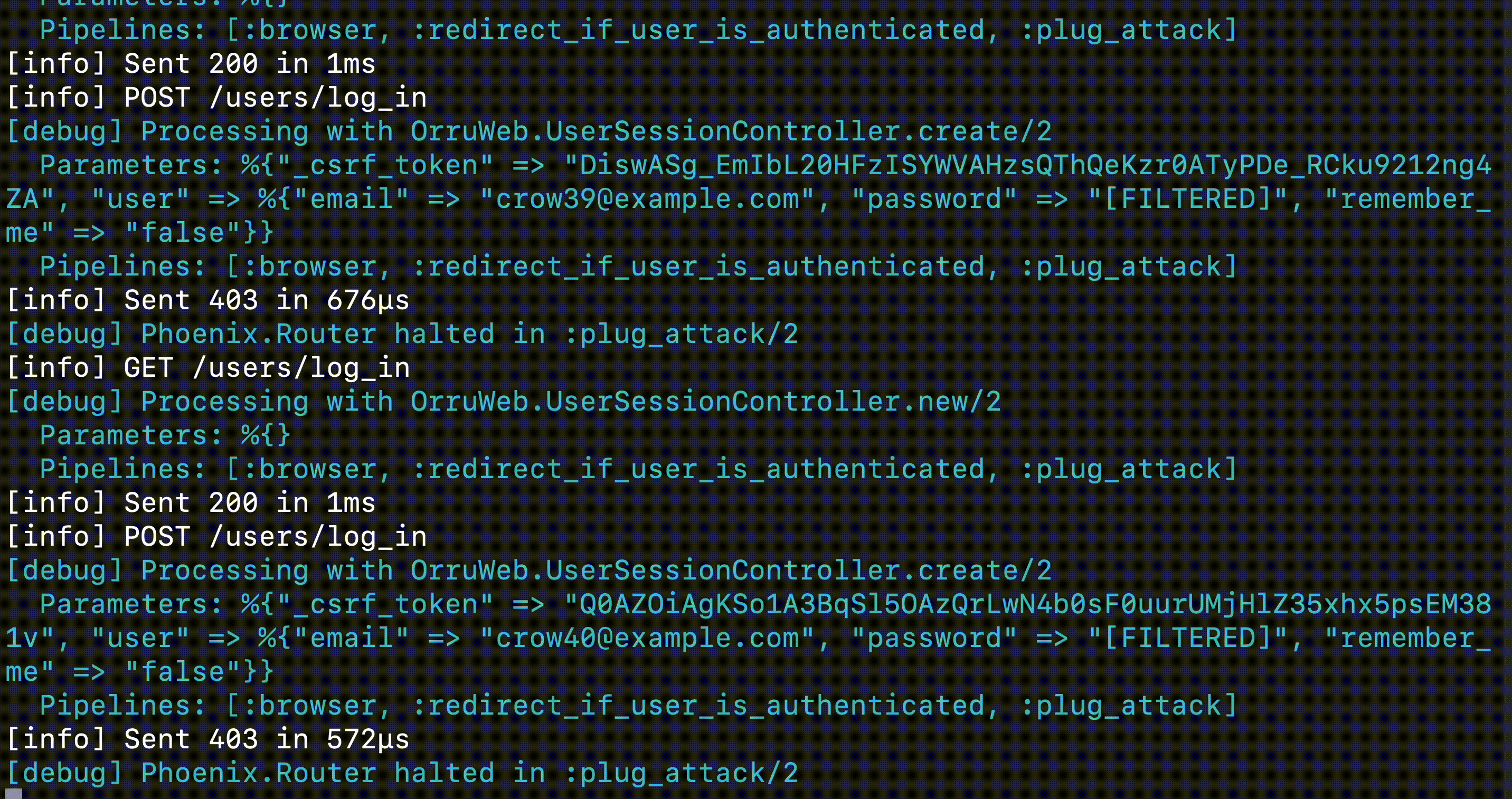
This post describes how an account takeover attack works, from the perspective of the attacker, and the owner of a victim Phoenix application. After the reader sets up the environment, we introduce PlugAttack, an Elixir library to throttle and ban clients who are abusing the login functionality.
Read next [File Format Verification] With Elixir
